Owasp Top 10 Vulnerabilities 2019 Pdf
Hashicorpterraform-provider-aws latest version 3. Beginners Quest - Web Solutions we covered the web challenges for the 2018 Google CTF which covered a variety of security issues ranging from topics such as the improper use of client side scripts and other simple vulnerabilities like cross-site scripting also known as XSS.
The OWASP Threat Dragon is an open-source solution that was released in 2016.

. Feb 21 2019 In my previous post Google CTF 2018. In 2016 server-side vulnerabilities did not even make the list of the top 10 most common threats. Penetration Testing Tools and Companies.
24 Jun 2019 We used terraform for this environment so the CloudFormation web ACL and rules are not being used and I will start be testing out the 10 Okt. The vulnerabilities found in the OWASP Juice Shop are categorized into several different classes. OWASP API Security Top 10 2019 stable version release.
Dedicated reports track project security against the OWASP Top 10 and CWE Top 25 standards. The security reports PDF export includes the project security overview and the top security reports. OWASP API Security Top 10 2019 pt-BR translation release.
Pentest tools scan code to check if there is a malicious code present which can lead to a potential security breach. Server vulnerabilities are no longer the main threat to mobile applications. In the Avast Threat Landscape 2019 Predictions Report Avast research shows that in 2018 60 of users around the world have never updated their routers firmware leaving them potentially vulnerable to fairly simple attacks that exploit firmware vulnerabilities This goes to show that the majority of people dont know how to protect.
The RC of API Security Top-10 List was published during OWASP Global AppSec Amsterdam. The RC of API Security Top-10 List was published during OWASP Global AppSec DC. 10 Best Data Loss Prevention DLP Tools for 2021.
It is very similar to MTTM with less focus on Microsoft-centered services. Most of them cover different risk or vulnerability types from well-known lists or documents such as OWASP Top 10 OWASP ASVS OWASP Automated Threat Handbook and OWASP API Security Top 10 or MITREs Common Weakness Enumeration. By segregating Security Hotspots from true Vulnerabilities we set developers expectations going in and maintain their confidence in the analysis.
Automated tools can be used to identify some standard vulnerabilities present in an application. Threat Dragon is a web-based tool though the older versions are desktop-based. Back in 2012 Weak Server Side Controls ranked second in the OWASP Mobile Top 10 rating.
Terraform output -no-color -json web_acl_name TestWafWebAclV2Sizeconstraint 2021-10-19T140641-0300 logger.
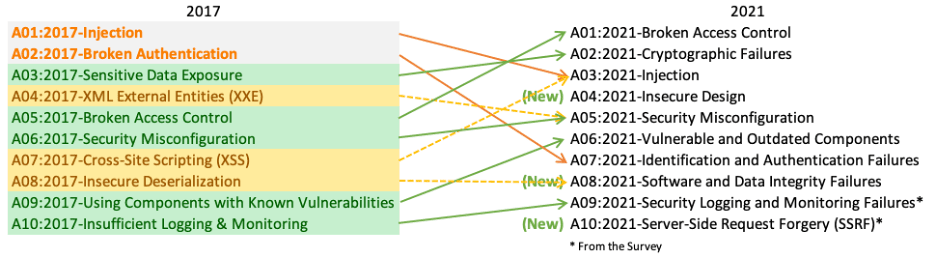
Owasp Top 10 2021 Is It The Right Direction Cydrill Software Security

Semestre Rottura Revoca Owasp Top Ten Accesso Escludere Caravan

Owasp Top 10 Vulnerabilities Application Attacks Examples

Semestre Rottura Revoca Owasp Top Ten Accesso Escludere Caravan

Top Ten Attacks By Owasp Top 10 2017 Download Scientific Diagram
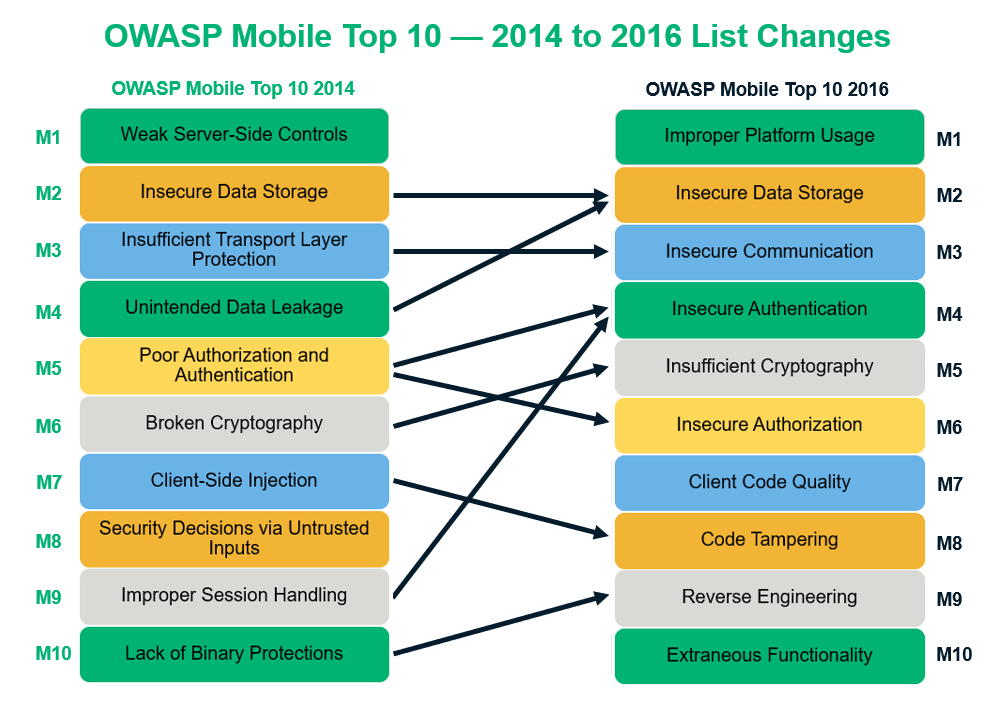
Owasp Mobile Top 10 Vulnerabilities Mitigation Strategies Infosec Insights
.pdf-5.jpg)


0 Response to "Owasp Top 10 Vulnerabilities 2019 Pdf"
Post a Comment